OpenDNS Plugs DNS Leaks on the “Last Mile” with DNSCrypt

OpenDNS has long provided safer, more reliable web browsing via an alternate DNS server. DNSCrypt adds even more security by encrypting your DNS traffic to stop “DNS leaks.”
Earlier, I wrote up OpenDNS, a free service that provides a faster, more secure way to resolve domain names. Now, OpenDNS is rolling out a new piece of software designed to make your web browsing even more secure: DNSCrypt.
DNSCrypt is an additional service layered on top of OpenDNS that helps protect against vulnerabilities presented by “DNS leaks.” It does so by encrypting DNS traffic to ensure that it can’t be intercepted by a hacker or a man-in-the-middle. This is similar to, but not the same as, HTTPS encryption of web traffic (SSL/TLS).
In a nutshell, OpenDNS improves your web browsing security by giving you greater assurance that the website you are connecting to is the one you intended to connect to. It does so by providing a better DNS server than the one your ISP provides by default. Once your request reaches the OpenDNS servers, you can be reasonably assured that you’re making a legitimate connection to the website you’re trying to reach. But this still leaves one relatively weak link in the chain: the “last mile” or, the portion of your Internet connection between your ISP and your computer. That is, hackers could still snoop or divert your DNS traffic by intercepting it before it reaches your ISP. With DNSCrypt, hackers won’t be able to snoop on your DNS traffic anymore—nor will they be able to trick your computer into thinking that you’re communicating with a legit DNS server.
Checking for DNS Leaks
The risk of someone eavesdropping on or spoofing a DNS in the “last mile” is very low. Basically, for this vulnerability to be present, you’d have to have a “DNS leak” on your connection. That is, even though you’ve set up your computer or router to connect to OpenDNS (or a VPN or alternate DNS server, such as Google DNS), something on your computer is still making requests to the default DNS server (usually your ISP’s).
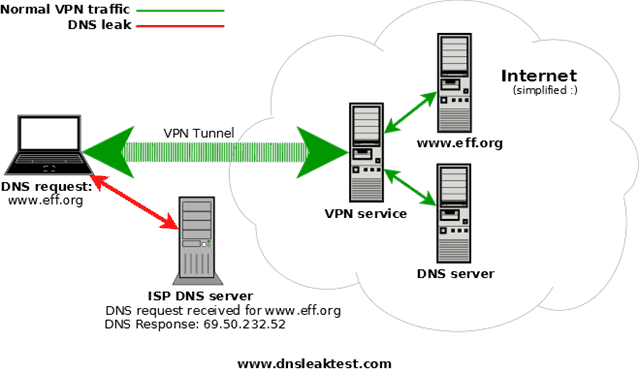

You can test to see if you have a DNS leak by visiting DNSleaktest.com while connected via OpenDNS. According to the folks at DNSleaktest.com, DNS leaks are most prevalent on Windows clients. However, I’m happy to report that my test for DNS leaks came up dry while connecting with OpenDNS on my Windows 8 computer.


Installing DNSCrypt
DNSCrypt is available for free as a Preview Release. In fact, the software is open source (you can view the source on GitHub). You can download DNSCrypt here. It is available for both Mac and Windows and is a breeze to install—just launch the installer and follow the on-screen prompts.
After installation, you’ll see a green indicator in your system tray showing you that DNSCrypt is working.

Right-click the icon to open the Control Center for more info and options.
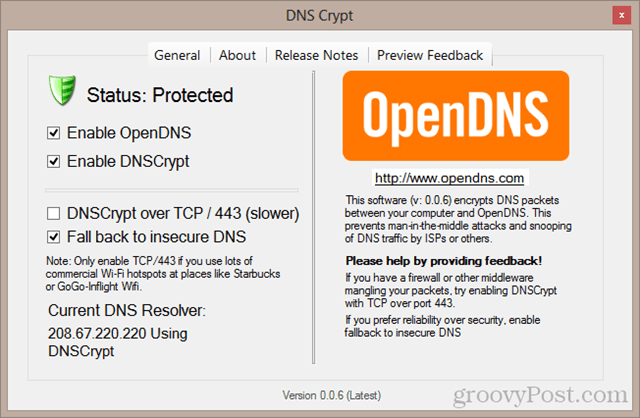

Note that once you install DNSCrypt, you won’t have to alter your DNS settings for your network adapter in order to use OpenDNS anymore. You can simply check Enable OpenDNS and your computer will begin using OpenDNS. This is handy if you haven’t set up your router to use OpenDNS.
The default settings (shown above) are optimized for speed and reliability. For example, if OpenDNS cannot be reached, your computer will fall back to your default DNS server. (Note: if OpenDNS is your default DNS resolver, then this option won’t make much of a difference).
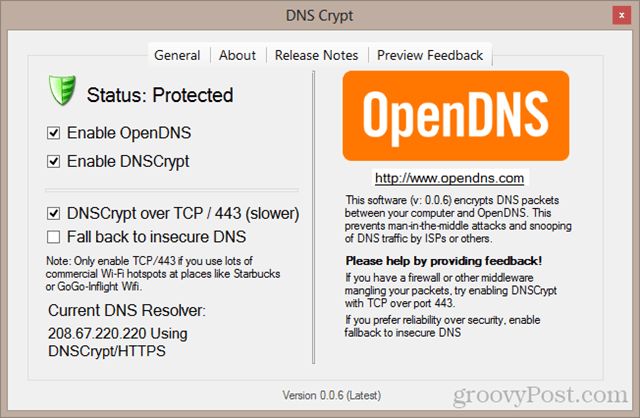
For the highest security, check DNSCrypt Over TCP / 443 (slower) and uncheck Fall back to insecure DNS. The settings shown below are safer when using public Wi-Fi.

Conclusion
Most home users won’t need DNSCrypt to keep them safe. The exploitation of DNS leaks is rare, and most connections do not exhibit this vulnerability (Macs, for example, aren’t known to have DNS leaks). However, if a private, secure connection is of utmost importance to you—whether for personal or business reasons—DNSCrypt is a free and painless way to add one more layer of security to your PC’s connection,
Did you know about DNS leaks? Will you use DNSCrypt? Let us know in the comments.
5 Comments
Leave a Reply
Leave a Reply

Si
June 10, 2013 at 10:13 pm
Thought I would give this a try but cannot install. The downloaded file seems to be misnamed (a 6{1} file type apparently). Anyway, Windows 8 doesn’t know what to do with it and nor do I!
Alexmvp
June 11, 2013 at 7:22 am
I’m a huge fan of OpenDNS and I’m surprised groovypost doesn’t talk about it more. I always get questions at work about how to block porn and other sites for kids and this just works.
you guys need to write that up so I can just point vs. have to explain it every time.
signed,
a demanding reader!
Alexmvp
June 11, 2013 at 7:24 am
Oh and thanks for this awesome article Jack. Love your stuff… I’m a huge fan of opendns and now I’m an even larger fan (symbolically, not physically) not that I know about DNS Crypt. Very cool.
Why do you think they are offering all these free services?
Brian Burgess
June 11, 2013 at 3:22 pm
@Alexmvp
This should work: https://www.groovypost.com/howto/block-websites-social-networking-porn-using-opendns/
You might also want to point them to Jack’s article on how to set up OpenDNS:
https://www.groovypost.com/howto/setup-opendns-home-network-router/
Thanks for reading!
Frank Denis
June 14, 2013 at 2:41 pm
Please see http://dnscrypt.org for more info about dnscrypt, including up to date versions and correct links.