How to Check the Strength of Your Passwords

Do you use a secure password with your important online accounts? Ever wondered exactly how good it is? Here’s how to check password strength.
We’ve talked about creating strong passwords in multiple articles over the years… but we’ve never given you a way to test them. So, let’s first dig into what makes a secure password and then review a few sites which we recommend to test your passwords with.


What is Password Entropy?
Entropy is the level of unpredictability for a password. Or, in other words, the higher the entropy, the more secure your password is.
To understand the basics of how long a password would take to crack vs. its amount of entropy, there is a very simplified formula to follow. Please note that this is a very, very simplified explanation but here it goes.
- 2^(the level of entropy) = number of guesses needed to crack.
- Any average Joe can install password-cracker software and make about 1000 guesses per second.
- Divide # of guesses needed by guesses-per-second and you have the seconds of time required to crack the password, just divide according to days/hours/minutes.
- However, if we speed that up to crazy supercomputer levels (like this guy who built a 25-GPU machine that can do 350 billion guesses per second), it becomes a lot quicker. But, the guess rate is significantly slowed down depending upon which encryption algorithm is used. The typical website uses SHA1, which a supercomputer could crack at a rate of 63 billion guesses per second.
Keep in mind that while these passwords are stored on a web server, they are usually protected by a maximum number of password attempts over a certain amount of time. But, if the website ever gets hacked then its password hashes can be easily run through any offline cracking system that the hackers have set up.
Cygnius Password Strength Test
Of the available tools, the Cygnius Password Strength Test is my favorite. It’s just a simple box, and when you type in the password, it will tell you its strength, the character set, and its level of entropy.
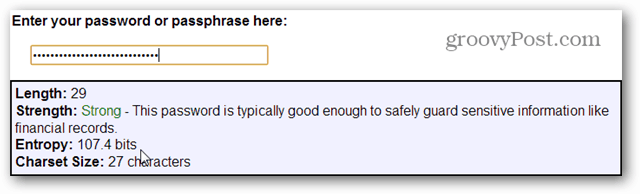

For example:
- “tr0G0d4r” = 35.5 bits of entropy
35.5 bits of entropy = 398 days for the average Joe to crack, but only 0.5 seconds for a supercomputer to break. That translates to less than a minute for almost any cracking expert out there to break in!
- “mygmailpassword” = 58.9 bits of entropy
58.9 bits of entropy = 18,267,344 years for the average Joe password crack to break. Or on a supercomputer about 105 days, in theory.
- “i have a very strong password” = 107.4 bits of entropy
107.4 bits of entropy = 5,141,800,300,000,000,000 millennia for the average Joe password cracker to break. On a supercomputer, it would take 81,615,877,245 millennia to crack. It is highly unlikely it will ever be cracked unless your password is singled out and targeted by multiple systems.
Other sites that can test your password strength
4 Comments
Leave a Reply
Leave a Reply

Simon H
April 22, 2013 at 10:06 am
Rumkin looks useful for checking strength against a pure brute force attack and the information warns against using common or repetitive passwords / phrases but passwordpasswordpasswordpassword is classed as very strong 128.7 bits with no warning of it being repetitive.
Thequickbrownfoxjumpsoverthelazydog 165.4 bits with no warning that it’s a common phrase.
qwertyuiop was considered reasonable with 37.3 bits and no warning of it been a common password.
Not dissing Rumkin, I just thought I would point this out as these are passwords I have seen people using, qwertyuiop on more than one occasion.
Robb S.
June 17, 2014 at 1:29 pm
The real problem with all of these PW strength testers is they all assume a brute force attack, with some adding on variables for a dictionary attack. Whoever, sophisticated crackers usually incorporate multiple cracking tools such as rainbow tables, cryptanalysis, and hybrid attack tools, to help speed up the cracking process. The only real method of creating a strong password is using a long Pass Phrase – stringing three or more words together based upon something only the end-user knows
Ziggy
October 6, 2017 at 7:59 pm
I tried a variant of one of my passwords and I’m told that it would take 10 quintillion years to crack!
I’m happy with that. On a more serious note, great comments from Robb S and Simon H. Very interesting article, indeed. Thanks Austin…
Clay Ziegler
October 7, 2017 at 7:17 am
Mr. Austin Krause,
Your friends at “Strength Test” don’t offer a secure link for their site. That, in itself, bothers me.
You might want to suggest to them that they implement a secure connection.
Here’s a site I prefer over yours: “How Secure is My Password.” It is a secure site, and it is far “cleaner” than “Strength Test’s” site.
Also, “The Password Meter,” although, it too, like the “Strength Test” site, is an unsecured site, is less “cluttered;” and easier “on the eye,” than the “Strength Test” site.
I found multiple password testing sites online, that all used a secure connection, and were far less “cluttered,” and easier “on the eye” than your choice. With all of the above being said; what attributes of the “Strength Test” site made you decide that it would become your favorite (“Of the available tools, Rumkin’s strength test is my favorite.”)?
Regards,
Clay Ziegler
Writer/Copywriter/Editor